 "Virus" courtesy of [Yuri Samoilov via Flickr]
"Virus" courtesy of [Yuri Samoilov via Flickr]
Technology
Ransomware: Holding Our Digital Lives Hostage?
A hospital in Los Angeles, the Hollywood Presbyterian Medical Center, recently agreed to pay a ransom of $17,000. But the ransom wasn’t paid to free some worker held hostage or to prevent the release of a catastrophic pathogen. Instead it was handed over to hackers for the safe return of its patients’ medical files. Hackers managed to penetrate the hospital’s computers and encrypt its files, and demanded a large sum to be paid in the form of Bitcoins. While this scenario sounds far-fetched, this type of crime is actually on the rise. Read on to find out more about ransomware, bitcoins, why these types of attacks are increasing, and what can be done to stop them.
What is Ransomware?
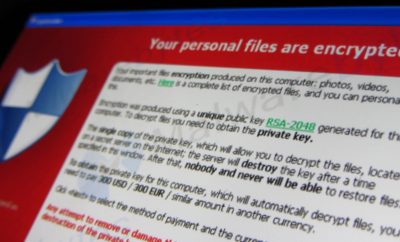
Ransomware is a type of malware employed by hackers to stop users from accessing their own information or data. It does this in one of two ways. Either a screen is locked and instructions are provided for unlocking it, or important information is encrypted and a password or key known only to the hackers is required to reopen the essential information. While the exact date of ransomware’s origin is non-definite, it appears to have started in Russia sometime around 2006, spreading globally by 2012.
By 2013, ransomware hackers were using encryption through something known as CryptoLocker. Before encryption, ransomware typically blocked people from using their computers or tricked users into paying to regain access to their computers. An example of this is Reveton, which shows notifications claiming to be from a law enforcement agency, informing the user that a crime has been committed and a fine must be paid. But such malware could be uninstalled or removed with an antivirus program, though even that can be particularly difficult. When encryption came on the scene, hackers began encrypting files, making it impossible for users to access their own information without an encryption key. Even if the ransomware is removed, the files remain encrypted. This key element of ransomware is what makes it both very dangerous and lucrative, as it can be removed yet continue to do damage.
In 2014, ransomware hackers also began using the Tor network to remain anonymous. Tor is a unique network that does not directly plug into the internet, connecting through a series of servers instead. Hackers began using this network to communicate with command and control servers that store the encryption key, which can be sent to an infected computer after a ransom is paid. Doing so makes it nearly impossible to track an attack to an individual because their identity is concealed throughout the process.
The accompanying video gives a quick look at what ransomware is:
Payment
Paying the ransom part of ransomware is also an increasingly complex process. In the case of ransomware like Reveton, hackers often request payment through several services that are difficult to trace such as UKash, PaySafeCard, and MoneyPak. But a growing trend among these hackers has been to request the money in Bitcoins, which is how the hospital in Los Angeles paid its ransom. Bitcoin is a type of cryptocurrency that exist entirely online with no physical presence. Bitcoins are not controlled by a central bank and are based on mathematics, making it completely decentralized and not tied to the value of a commodity like gold or silver. Bitcoin is particularly attractive to hackers because of the anonymity it provides.
Growing Popularity of Ransomware
The threat of ransomware is also on the rise. As of January 2013, there had been 100,000 such attacks but by the end of that year alone that number rose to nearly 600,000, according to Antivirus software company Symantec. Symantec also looked at data from command and control servers used by ransomware hackers to estimate how profitable these scams really are. According to its calculations, hackers can earn around $33,600 per day, amounting to as much as $394,000 in a month. Two primary questions remain: how do hackers select targets and why are attacks increasing?
To answer the first question, targets so far have generally been chosen at random, although future hackers could research a target beforehand to find the most lucrative one. While targets are generally chosen at random, many victims have been infiltrated by viruses or spyware before, suggesting that certain victims may be chosen simply because their systems are easy to penetrate. Traditionally, these random targets were individuals who paid small sums, but recently, the size of the target and the requested ransoms have increased. Conventional wisdom on the use of ransomware is also changing as the payment for these random attacks has shifted more and more to Bitcoins.
Bitcoins help answer the second question–why are ransomware attacks on the rise? While Bitcoin is completely transparent when it comes to transactions, it is often very difficult to trace a Bitcoin address back to an individual, making it easy for hackers to remain anonymous. The rise of Bitcoin has given hackers a reliable and anonymous method to receive ransom payments, which likely contributes to the rise in ransomware attacks.
The video below comments on the attack in LA and the rise of such attacks:
Stopping Ransomware
So with ransomware attacks increasing, how can people avoid falling victim? There are several steps any user can take to eliminate or, at least, mitigate their exposure to dangerous ransomware. First is to use a reputable anti-virus software to help prevent and remove malicious programs. But reputation is important, as there are many fake options that may actually give your computer a virus. Similarly, it is important to make sure your computer’s existing firewall is strong and activated.
Even with anti-virus software in place and a strong firewall, it is still paramount to be cautious. Using a pop-up blocker and being careful when opening email attachments is also an important way to avoid exposure. It is additionally important to back up files and information regularly. If you have a backup of your files in the cloud or on an external hard drive, you will still have access to your information even after it is encrypted by ransomware.
In the event of a ransomware attack, it is also important to get the authorities involved, including the FBI, as ransomware is generally beyond the scope of local police departments. In fact, the police themselves are not immune to attacks either, as police departments in both the Boston area and in Maine fell victim and paid subsequent ransoms.
So far, the FBI has actually had some success fighting ransomware. In 2013, for example, it stopped the software platform Citadel, which was behind the Reveton-style ransomware attacks. In 2014, the FBI also disrupted a major botnet–a network of computers used to infect computers with malware– and seized control of the servers behind CryptoLocker. While the FBI has had some success fighting these hackers, in certain cases the bureau says the best way to fight ransomware is to actually pay the ransom. While this goes against the conventional wisdom of not giving into criminals’ demands, the encryption used is often nearly impossible to crack and the requested ransoms may be relatively small. Put simply, for some people its often easier to just pay up.
Conclusion
Not only is ransomware on the rise, it is becoming much harder to combat and hackers are moving to even more lucrative targets. While it is bad enough that individuals often have to deal with ransomware, hackers are now starting to go after essential institutions such as police departments and hospitals. While targets take on an ever-growing importance, the reality is that ransomware is not going away anytime soon. In many respects, ransomware is not that different from other types of malware, with the exception that it offers to restore the user’s capabilities for the right price. As is the case with other malware, ransomware shows no signs of fading. Its methods are becoming more effective and recovering payments is easier than it has ever been.
Unfortunately, potential targets and those already affected have little recourse in this battle. While the FBI has made some progress, even it suggests that paying up for relatively small amounts may be victims’ best option. An important question going forward is how to respond if hackers increasingly target important institutions. And as the profiles of these targets increase, will the ransoms increase as well?
Resources
Symantec: Ransomware: A Growing Menace
Tech Times: LA Hospital Hit By Ransomware Pays Hackers $17,000: Is It The Right Choice
Phys.org: Why Ransomware is on the rise
Norton: Beware the Rise of Ransomware
Federal Bureau of Investigations: Ransomware on the Rise
The Security Ledger: FBI’s Advice on Ransomware? Just Pay The Ransom







Comments